The Surprise Verification Screen
You’re rushing to check an important email, enter your Gmail credentials, and suddenly hit a wall: “Verify your identity by adding a phone number.” This unexpected screen can feel like being locked out of your own digital life. One moment you’re accessing your inbox normally, the next you’re staring at a verification prompt that wasn’t there yesterday.
Many Gmail users encounter this security checkpoint without warning, leaving them confused and frustrated. Why is Google suddenly asking for your phone number? What triggered this verification requirement? Most importantly, how can you regain access quickly and prevent future lockouts?
This comprehensive guide explains exactly when Gmail triggers phone verification, the security reasons behind these prompts, and provides step-by-step solutions to get back into your account. You’ll also discover proven strategies to maintain seamless Gmail access while keeping your account secure.
Understanding Gmail phone verification isn’t just about solving today’s problem – it’s about building long-term account resilience and avoiding future access issues.
Common Triggers for Gmail Phone Verification
Suspicious Login Attempts
Gmail’s security algorithms constantly monitor login patterns for unusual activity. The system flags attempts from unrecognized devices, unfamiliar IP addresses, or locations that don’t match your typical usage patterns.
If you recently traveled abroad and tried accessing Gmail from a hotel WiFi, the system detected this location mismatch and triggered verification. Similarly, logging in from a friend’s computer or a public library device often prompts phone verification because Google doesn’t recognize the hardware fingerprint.
Network-level changes also raise red flags. Switching internet service providers, using a new router, or connecting through different cellular towers can alter your digital footprint enough to trigger security measures.
Multiple Failed Login Attempts
Wrong password entries – whether from forgotten credentials, typos, or autocomplete errors – signal potential unauthorized access attempts to Gmail’s security system. Even legitimate users who misremember their password can accidentally trigger verification protocols.
Gmail implements progressive security measures: a few wrong attempts might just delay your next login, but persistent failures activate phone verification as a protective barrier against brute-force attacks. This system effectively blocks automated bots while allowing real users to prove their identity through phone confirmation.
The verification threshold varies based on account history, but typically activates after 3-5 failed attempts within a short timeframe.
New Device or Browser
First-time logins from fresh devices almost always trigger Gmail phone verification. This includes new smartphones, tablets, computers, or even familiar devices after major software updates that change their digital signatures.
Browser-related triggers are equally common. Installing a new browser, clearing cookies and cache, using incognito mode, or updating browser software can make your device appear “new” to Google’s recognition systems.
Even switching between Chrome, Firefox, Safari, or Edge on the same computer can prompt verification if you haven’t logged into Gmail from that specific browser before.
High-Risk Activity
Gmail monitors sending patterns and account usage for signs of compromise or abuse. Sudden spikes in email volume, especially to multiple recipients, can trigger verification requirements to prevent spam distribution from compromised accounts.
Accessing sensitive Google services amplifies security scrutiny. Attempting to modify payment information, access Google Workspace admin panels, or make significant account changes often requires additional identity confirmation through phone verification.
Business users frequently encounter verification when switching between personal and professional Google accounts, particularly when accessing organizational data or collaborative documents with sensitive information.
Why Gmail Uses Phone Verification
Account Security
Phone verification serves as Gmail’s primary defense against unauthorized access. Your phone number acts as a unique identifier that’s significantly harder for attackers to compromise compared to passwords alone.
This verification method provides two-factor authentication backup when your primary security measures fail. Even if someone discovers your password through data breaches or phishing attempts, they still need physical access to your phone to complete the login process.
Google’s security research shows that phone verification prevents over 99.9% of automated attacks and dramatically reduces successful account takeovers. This protection becomes especially critical for accounts containing sensitive personal information, financial data, or business communications.
Spam and Abuse Prevention
Automated systems constantly attempt to create fake Gmail accounts for spam distribution, phishing campaigns, and other malicious activities. Phone verification creates a significant barrier for these automated account creation attempts.
Each phone number can only verify a limited number of Gmail accounts, preventing mass account generation from single sources. This limitation effectively disrupts spam operations that rely on disposable email addresses.
Gmail also uses phone verification to detect unusual sending behavior from existing accounts. If your account suddenly starts sending bulk emails with spam-like characteristics, verification requirements help confirm that legitimate account owners are responsible for the activity.
Compliance and Policy Requirements
Regional anti-spam laws and data protection regulations often require email providers to implement robust identity verification systems. Phone verification helps Gmail comply with these legal requirements while maintaining service availability across different countries.
International regulations like GDPR in Europe and CAN-SPAM in the United States mandate specific security measures for email services. Phone verification demonstrates Gmail’s commitment to protecting user identity and preventing abuse of their platform.
Certain countries have mandatory verification requirements for email accounts, making phone confirmation a legal necessity rather than just a security preference.
How to Handle Gmail Phone Verification
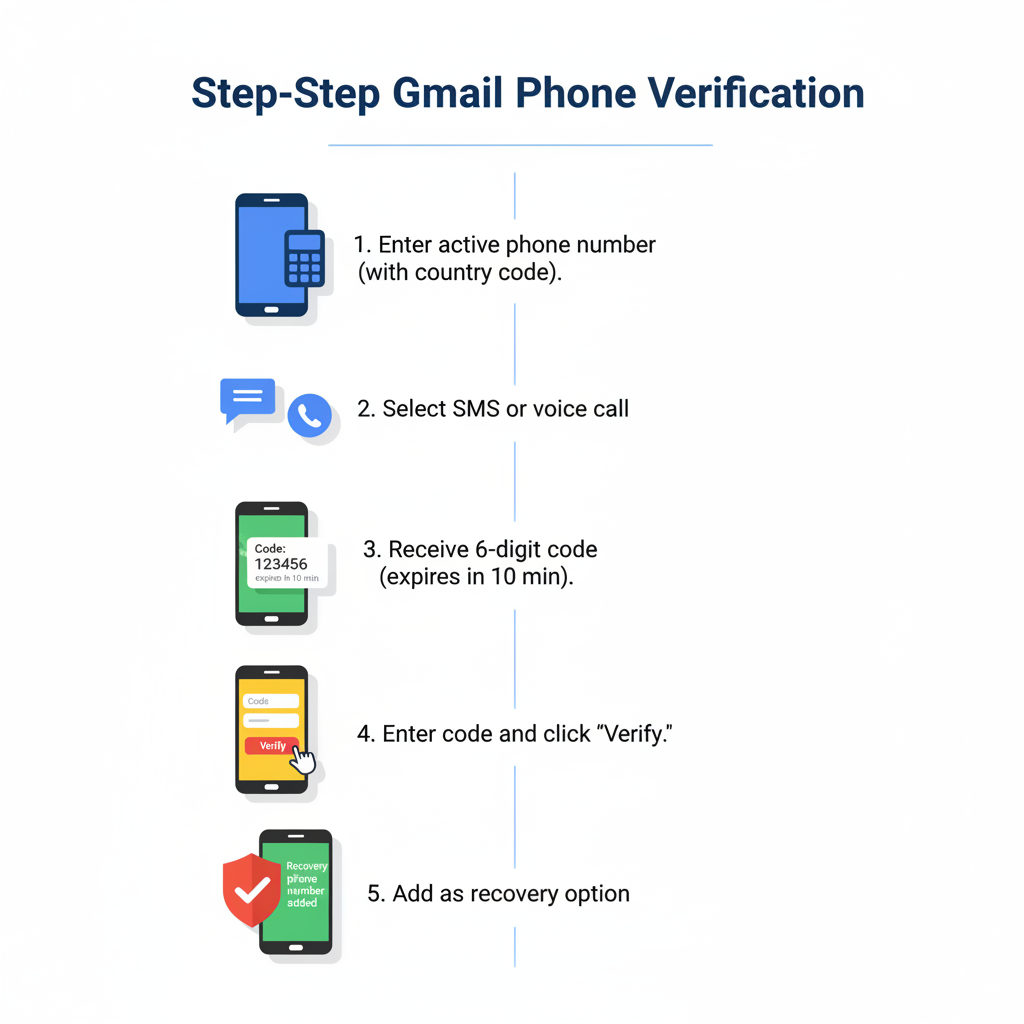
Step-by-Step Response
Step 1 → When Gmail presents the phone verification screen, enter your current, active phone number in the provided field. Use the full number including country code if you’re outside the United States.
Step 2 → Choose between SMS text message or voice call verification. SMS is typically faster, but voice calls work better for users with messaging issues or older phones.
Step 3 → Check your phone for the verification code within 2-3 minutes. The code usually arrives as a 6-digit number that expires after 10 minutes for security reasons.
Step 4 → Enter the verification code exactly as received, then click “Verify” to complete the process and regain Gmail access.
Step 5 → Once verified, Gmail may ask if you want to add this number as a recovery option. Accept this to streamline future verification processes.
When to Contact Support
If verification codes consistently fail to arrive, first check your phone’s signal strength and messaging capabilities. Network congestion or carrier issues can delay SMS delivery, especially during peak usage times.
Lost access to your verification phone number requires alternative recovery methods. Use Gmail’s account recovery form, which guides you through identity confirmation using backup emails, security questions, or previous password information.
Contact Google Support directly when standard recovery methods fail. Provide detailed account information including recent email activity, contact lists, and account creation details to help verify your identity through alternative means.
Business and Google Workspace users should contact their IT administrators first, as organizational accounts often have additional recovery options and administrative override capabilities.
Avoiding Future Lockouts
Keep your recovery information current and easily accessible. Update phone numbers immediately when switching carriers or getting new devices. Add multiple recovery methods including backup phone numbers and alternative email addresses.
Enable two-step verification proactively rather than waiting for forced verification. This gives you control over security settings while maintaining consistent access patterns that Gmail’s algorithms recognize.
Use Google’s Security Checkup tool quarterly to review and update all account security settings. This proactive approach identifies potential issues before they cause access problems.
Preventing Unnecessary Verifications
Maintain Consistent Login Habits
Establish regular Gmail access patterns using trusted devices and familiar network connections. Consistent behavior reduces the likelihood of triggering security algorithms that interpret changes as potential threats.
Avoid frequent VPN switching or proxy server usage, which can make your location appear to jump between countries rapidly. If you must use VPNs, try to use the same server locations consistently.
Use the “Remember this device” option when Gmail offers it during successful logins. This helps Google recognize your devices and reduces future verification requirements.
Update Recovery Information
Maintain current backup contact methods for your Gmail account. Add secondary phone numbers, alternative email addresses, and ensure recovery information reflects your current situation.
Review and update security settings whenever you change phone numbers, move to new locations, or modify your typical internet usage patterns. Proactive updates prevent access disruptions.
Add trusted devices to your Google account through the security settings. Pre-authorized devices experience fewer verification prompts and provide smoother access experiences.
Follow Google’s Security Best Practices
Implement strong, unique passwords for your Gmail account using password managers to avoid forgotten credential issues that trigger verification. Strong passwords also reduce the risk of unauthorized access attempts.
Enable two-step verification with Google Authenticator or similar apps. This provides security benefits while giving you more control over the verification process compared to reactive phone verification.
Regularly review account activity logs to identify and address unusual access patterns before they trigger automatic security responses.
Special Cases and Regional Differences
New Account Creation
Phone verification during Gmail account creation has become standard practice, especially for users creating multiple accounts or accessing from shared networks. Google requires phone numbers to verify identity and prevent automated account generation.
Each phone number has limits on how many Gmail accounts it can verify, typically ranging from 3-5 accounts depending on the region and account types. Business users often need dedicated phone numbers for professional account creation.
Temporary or virtual phone numbers rarely work for Gmail verification, as Google’s systems detect and block most disposable number services.
Business and Workspace Accounts
Google Workspace accounts face stricter security requirements due to organizational data protection needs. Business account verification often requires additional steps including admin approval and enhanced identity confirmation.
IT administrators can configure organization-wide verification policies that override individual user preferences. These policies might require phone verification for all users or specific user groups handling sensitive information.
Workspace users switching between personal and business accounts frequently encounter verification prompts due to the different security profiles and access patterns associated with each account type.
International Access Issues
Traveling abroad commonly triggers Gmail phone verification due to sudden location changes and unfamiliar network connections. International roaming can also affect how verification codes are delivered.
Some countries have specific requirements for email account verification, making phone confirmation mandatory regardless of user preferences or account history. These requirements vary by region and can change based on local regulations.
Cross-border internet routing sometimes makes domestic logins appear international to Google’s systems, inadvertently triggering verification requirements for users who haven’t actually traveled.
Conclusion & Expert Recommendations
Quick Recap of Triggers
Gmail phone verification typically occurs due to suspicious login attempts from unrecognized devices, multiple failed password entries, or access from new locations. High-risk activities like bulk emailing or sensitive account changes also trigger verification requirements.
New device logins, browser changes, and cleared cache/cookies consistently prompt verification as security measures. International access and unusual network connections raise additional red flags in Google’s security algorithms.
Business accounts and new account creation face stricter verification requirements due to enhanced security needs and abuse prevention measures.
Building Gmail Account Resilience
Maintain current recovery methods including backup phone numbers and alternative email addresses. Regular security checkups prevent access disruptions and keep your account protection up to date.
Enable two-step verification proactively to gain control over security processes while reducing reactive verification requirements. Use consistent login habits and trusted devices to establish recognizable usage patterns.
Update recovery information immediately when changing phone numbers, moving locations, or modifying internet service providers. Proactive maintenance prevents lockouts and ensures smooth Gmail access.
Remember: Gmail phone verification protects your account from unauthorized access and abuse. While temporarily inconvenient, these security measures safeguard your digital communications and personal information from increasingly sophisticated threats.
Act quickly to secure your account by implementing these recommendations today. Your future self will thank you when you maintain seamless Gmail access while keeping potential attackers locked out.