The Hidden Barrier at Sign-Up
You’re ready to create a new email account, excited to set up your digital communications, when suddenly you hit an unexpected wall: “Please verify your phone number to continue.” This mandatory phone verification has become the silent gatekeeper that frustrates millions of users worldwide.
The problem is widespread and growing. Major email providers increasingly force phone number verification during sign-up, leaving users feeling trapped between privacy concerns and the need for essential email services. Some users don’t want to share personal phone numbers, others lack reliable phone access, and many simply prefer keeping their communications separate from mobile devices.
But you’re not stuck. Multiple email providers still allow sign-up without phone verification, and proven workarounds exist for services that typically require phone numbers. This comprehensive guide reveals exactly which providers respect user privacy, step-by-step methods to bypass phone verification when possible, and expert strategies to secure your accounts safely.
These insights come from tech industry experts, security researchers, and extensive user experience testing across dozens of email providers. You’ll discover actionable solutions that protect your privacy while ensuring reliable email access.
Why Email Services Ask for Phone Numbers
Security Concerns
Email providers implement phone verification primarily to combat spam and automated bot registrations. Phone numbers create a significant barrier for malicious actors attempting to create thousands of fake accounts for spam distribution, phishing campaigns, or other abusive activities.
Phone verification also streamlines account recovery when users forget passwords or lose access to their accounts. A verified phone number provides a direct recovery method that’s typically faster and more reliable than alternative verification processes like security questions or backup emails.
Providers argue that phone verification reduces customer support costs by preventing account lockouts and simplifying identity confirmation. Users with verified phone numbers experience fewer access issues and can recover compromised accounts more quickly than those relying solely on password-based security.
Abuse Prevention
Phone numbers limit the creation of multiple accounts from single sources, making it harder for spammers and fraudsters to operate at scale. Each phone number can typically verify only a limited number of accounts, creating natural constraints on mass account creation.
This verification method helps email providers detect and prevent coordinated abuse campaigns where attackers create numerous accounts for malicious purposes. Phone verification requirements significantly increase the cost and complexity of large-scale email abuse operations.
Financial fraud prevention also drives phone verification adoption. Email accounts connected to verified phone numbers provide additional identity confirmation for services involving payments, financial transactions, or sensitive personal information.
Regional Compliance
Legal requirements in certain countries mandate phone verification for email services. Anti-spam laws, data protection regulations, and national security policies often require email providers to implement robust identity verification systems.
European Union regulations like GDPR, while focused on privacy protection, paradoxically encourage some verification methods to ensure proper data handling and user consent. Some regions require phone verification to comply with local telecommunications and internet service laws.
International email providers often apply the strictest regional requirements globally to maintain consistent policies across all markets, rather than implementing region-specific verification systems that complicate their operations.
Providers That Allow Sign-Up Without Phone Verification
Popular Global Providers
Gmail occasionally allows sign-up without phone verification, particularly when accessed from desktop browsers rather than mobile apps. The requirement varies based on factors including location, device type, and current security policies, but users can often click “Skip” or “Not now” when prompted for phone verification.
Outlook and Hotmail from Microsoft typically offer alternative verification methods during sign-up. Users can often choose recovery email verification instead of phone numbers, especially when creating accounts through web browsers rather than mobile applications.
Yahoo Mail frequently allows account creation without mandatory phone verification, though the option may be less prominent in their sign-up flow. Yahoo often presents phone verification as recommended rather than required, allowing users to proceed with email-only verification.
These major providers balance security requirements with user accessibility by offering phone verification as strongly recommended rather than absolutely mandatory in many cases.
Privacy-Focused Providers
ProtonMail champions user privacy by allowing account creation without phone verification. This Swiss-based service focuses on end-to-end encryption and minimal data collection, making phone numbers optional rather than required for most account types.
Tutanota provides secure email services without mandatory phone verification, emphasizing privacy protection and user anonymity. Users can create accounts using only email addresses and strong passwords, with optional two-factor authentication available later.
Mailfence offers Belgian-based secure email services with flexible verification requirements. Phone numbers are optional during sign-up, and users can secure their accounts through alternative methods including recovery emails and security keys.
These privacy-focused providers explicitly design their services to minimize personal data collection while maintaining security through alternative verification methods and strong encryption protocols.
Niche and Alternative Providers
Zoho Mail provides professional email services with flexible verification requirements, often allowing business and personal account creation without mandatory phone verification. Their enterprise focus means they accommodate users who prefer alternative security methods.
GMX offers free email services with relaxed verification requirements, frequently allowing account creation through email verification alone. This German-based provider emphasizes accessibility over strict verification protocols.
Temporary and disposable email services like 10MinuteMail, Guerrilla Mail, and TempMail require no verification whatsoever, providing instant email addresses for short-term use. While not suitable for permanent communications, these services excel for temporary needs without any personal information requirements.
Regional providers often have different verification policies than global services, sometimes offering more flexible sign-up requirements for local users while maintaining security through alternative methods.
Step-by-Step Sign-Up Workarounds
Create Accounts Without a Phone Number
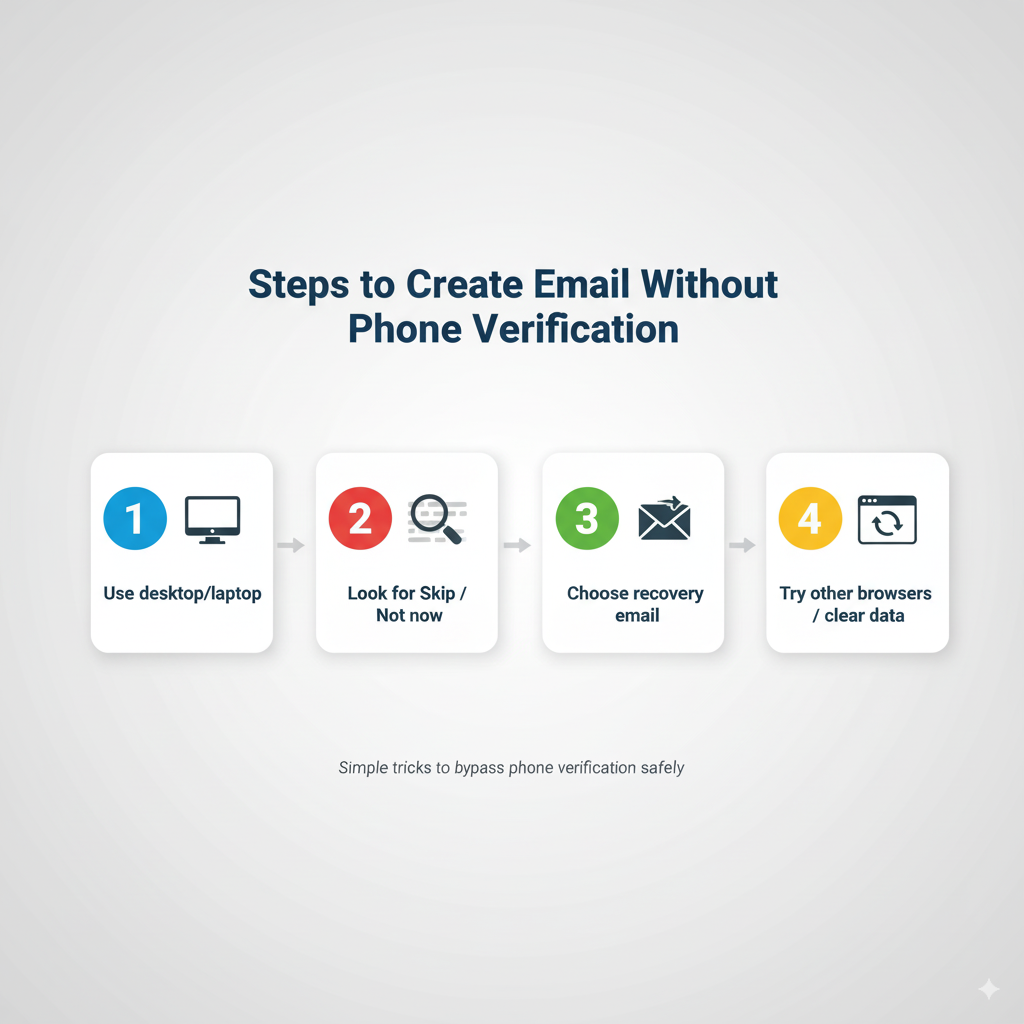
Step 1 → Choose desktop or laptop computers over mobile devices when creating email accounts. Many providers implement stricter verification requirements on mobile apps compared to web browser sign-ups, making desktop registration more likely to succeed without phone verification.
Step 2 → Look carefully for “Skip,” “Not now,” “I’ll do this later,” or similar options during the phone verification step. These options are sometimes displayed in smaller text or less prominent positions, but they’re often available even when phone verification appears mandatory.
Step 3 → Select recovery email verification when offered as an alternative to phone verification. Provide an existing email address that you can access to receive verification messages, ensuring you maintain account recovery capabilities.
Step 4 → Try different browsers or clear browser data before attempting sign-up. Some providers track previous sign-up attempts and may enforce stricter requirements for users who appear to be avoiding verification.
Regional & Device Tricks
Using VPN services to appear in regions with fewer verification requirements can sometimes bypass phone verification prompts. Countries with strong privacy laws or less stringent telecommunications regulations may have relaxed verification requirements for email sign-ups.
Switch between different browsers, devices, or internet connections when sign-up attempts fail. Providers sometimes implement device-specific or network-specific verification requirements that vary based on technical factors like browser fingerprinting or IP address reputation.
Attempt sign-ups at different times of day or week, as some providers implement dynamic verification requirements based on current security threat levels or registration volume patterns.
Using Secondary Options Safely
Avoid unreliable “fake number” services or temporary phone number generators for email verification. These services are often blocked by email providers, can disappear without notice, and provide no long-term account recovery capabilities.
Stick with recovery email addresses that you control and can access long-term. Use existing email accounts from different providers to create verification chains that ensure account recovery remains possible even if one service becomes inaccessible.
Consider using family or trusted friend phone numbers only if they agree and understand they may receive account recovery communications. Ensure you have alternative recovery methods available if this arrangement changes.
Risks and Limitations
When Skipping Phone Numbers Backfires
Accounts without phone verification face increased risk of permanent lockouts if passwords are forgotten or accounts become compromised. Email providers prioritize phone-verified accounts for recovery assistance, sometimes leaving non-verified accounts with limited recovery options.
Some email features may remain restricted or unavailable without phone verification. Advanced security features, increased storage limits, or integration with other services often require phone verification as a prerequisite.
Account security monitoring may be less comprehensive without phone verification. Providers use phone numbers for suspicious activity alerts and login notifications that help users detect unauthorized access attempts.
Best Practices for Safety
Always use strong, unique passwords for email accounts created without phone verification. Password managers help generate and store complex passwords that significantly improve account security when phone verification isn’t available.
Add recovery email addresses immediately after creating accounts without phone verification. Multiple recovery email addresses from different providers create redundant recovery paths that protect against single points of failure.
Enable two-factor authentication through authenticator apps when available, even if phone verification wasn’t required during sign-up. App-based 2FA provides strong security without requiring phone number disclosure to email providers.
Provider-Specific Caveats
Some email providers limit features or storage space for accounts created without phone verification. Free storage quotas, attachment limits, or sending restrictions may apply until phone verification is completed.
Regional policy differences mean verification requirements can change based on user location or provider policies. What works in one country or time period may not remain available as providers adjust their security requirements.
Business email providers often have stricter verification requirements than personal email services. Professional email needs may require accepting phone verification or choosing specialized business email providers with different policies.
Advanced Tips for Users
Disposable vs. Permanent Email
Temporary email services excel for one-time registrations, online purchases, or situations where long-term access isn’t required. Use disposable email for newsletter sign-ups, free trials, or any situation where spam is likely but ongoing access is unnecessary.
Permanent email accounts without phone verification work best when you need reliable, long-term communications but prefer privacy protection. Secure these accounts with strong passwords and recovery emails to ensure continued access.
Consider hybrid strategies that use disposable email for risky sign-ups while maintaining secure, permanent accounts for important communications. This approach balances convenience with security while protecting your primary email addresses.
Email for Business & Privacy
Professional users should avoid disposable email services for business communications, client relationships, or any situation requiring credibility and reliability. Temporary email addresses signal unprofessionalism and can harm business relationships.
Business email needs often justify accepting phone verification for improved security, customer support, and integration capabilities. Weigh privacy concerns against business requirements when choosing email providers for professional use.
Consider using email aliases from established providers rather than creating multiple accounts without phone verification. Aliases provide organizational benefits and privacy protection while maintaining the security and features of verified accounts.
Future Trends in Verification
Email providers continue adopting stricter verification requirements as spam, fraud, and abuse attempts increase. Expect more providers to implement phone verification as default rather than optional requirements.
Privacy-focused email services are growing in response to increased verification requirements from major providers. Demand for verification-free email options drives innovation in secure, privacy-respecting email services.
Alternative verification methods including biometrics, hardware keys, and blockchain-based identity systems may eventually reduce reliance on phone numbers while maintaining security standards.
Conclusion & Expert Recommendations
Quick Recap
Multiple email providers still allow sign-up without phone verification, including privacy-focused services like ProtonMail and Tutanota, major providers under certain conditions, and various niche alternatives that prioritize user accessibility.
Proven workarounds exist for bypassing phone verification on services that typically require it, including using desktop browsers, looking for skip options, and choosing recovery email verification when available.
Success requires balancing privacy preferences with security needs, understanding provider-specific limitations, and implementing strong account protection measures when phone verification isn’t available.
Smart User Strategy
Choose email providers based on your specific needs: privacy-focused services for sensitive communications, major providers for general use with maximum compatibility, or temporary services for short-term requirements.
Always implement recovery email addresses and strong passwords when creating accounts without phone verification. These security measures become especially critical when phone-based recovery isn’t available.
Balance privacy protection with practical security needs. While avoiding phone verification protects privacy, ensure you have reliable account recovery methods and understand the limitations of your chosen approach.
Stay informed about changing provider policies and maintain backup email options. Verification requirements evolve over time, and having multiple email providers ensures continued access even as individual services change their policies.
Create your email accounts strategically today, using these proven methods to maintain privacy while ensuring reliable, secure communications that serve your long-term needs.